PostgreSQL is an enterprise-grade, open source database management system. It supports both SQL and JSON for relational and non-relational queries respectively. Many companies in the market use PostgreSQL as their low-cost data warehousing solution in order to deliver efficient analytics and user insights.
Setting user permissions in PostgreSQL
After setting up your PostgreSQL database, create a user with the necessary privileges to create schemas and temporary tables in this database.
Run the following query to create a new user in PostgreSQL:
CREATE USER <username> WITH PASSWORD '<password>';Run the following query to grant permissions to the user to create new schemas and temporary tables in the database:
GRANT CREATE, TEMPORARY ON DATABASE <databasename> TO <username>;CREATE, TEMPORARY privileges to the user. Otherwise, RudderStack will not be able to export the events to PostgreSQL.Configuring PostgreSQL destination in RudderStack
To send event data to PostgreSQL, you first need to add it as a destination in RudderStack and connect it to your data source. Once the destination is enabled, events will automatically start flowing to PostgreSQL via RudderStack.
To configure PostgreSQL as a destination in RudderStack, follow these steps:
- In your RudderStack dashboard, set up the data source. Then, select PostgreSQL from the list of destinations.
- Assign a name to your destination and click Next.
Connection settings
- Host: Enter the host name of your PostgreSQL service.
- Database: Enter your PostgreSQL database name where RudderStack will load the data.
- User: Enter the name of the user created in the Setting user permissions in PostgreSQL section above.
- Password: Enter the password you set for the above user.
- Port: Enter the port number associated with your PostgreSQL instance.
- Namespace: Enter the schema name where RudderStack will create all the tables. If you don't specify any namespace, RudderStack will set this to the source name, by default.
- SSL Mode: Choose the SSL mode through which RudderStack will connect to your PostgreSQL instance. RudderStack provides three options - disable, require, and verify-ca. For more information on these options, refer to the SSL Modes section below.
- Sync Frequency: Specify how often RudderStack should sync the data to your PostgreSQL database.
- Sync Starting At: This optional setting lets you specify the particular time of the day (in UTC) when you want RudderStack to sync the data to the warehouse.
- Exclude Window: This optional setting lets you set a time window when RudderStack will not sync the data to your database.
- JSON Columns: Use this optional setting to specify the required JSON column paths in dot notation, separated by commas. This option applies to all the incoming
trackevents for this destination.
Configuring the object storage
RudderStack lets you configure the following object storage configuration settings while setting up your PostgreSQL destination:
- Use RudderStack-managed object storage: Enable this setting to use RudderStack-managed buckets for object storage.
Choose your storage provider: If Use RudderStack-managed object storage is disabled in the dashboard, select the cloud provider for your object storage and enter the relevant settings:
- Amazon S3 bucket storage settings
- Azure Blob Storage settings
- Google Cloud Storage bucket settings
- MinIO bucket storage settings
SSL modes
Based on your security preferences, RudderStack lets you specify the SSL mode through which you can send the data to PostgreSQL.
RudderStack supports the following three SSL modes defined by PostgreSQL:
| SSL mode | Eavesdropping protection | MITM (Man in the middle) protection | Description |
|---|---|---|---|
| disable | No | No | SSL mode is disabled. Use it in cases where security is not an issue and you don't want the encryption overhead. |
| require | Yes | No | Use this mode when you want to encrypt your data and can deal with the resulting encryption overhead. |
| verify-ca | Yes | Dependent on the CA policy | Use this mode when you want to encrypt your data, can bear the encryption overhead, and want to be sure that you connect to a server you trust. |
Using verify-ca to configure PostgreSQL destination
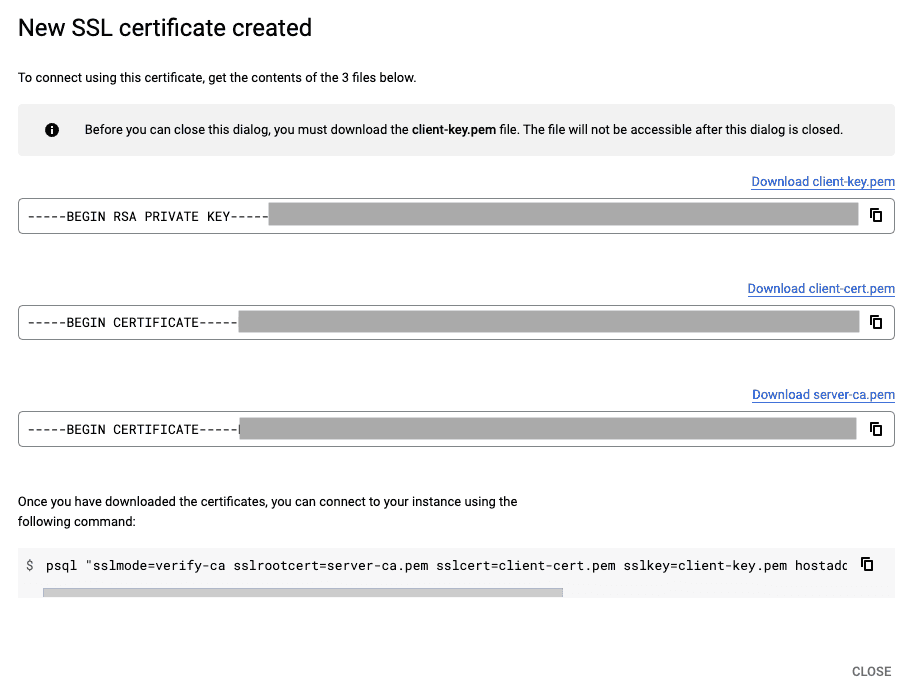
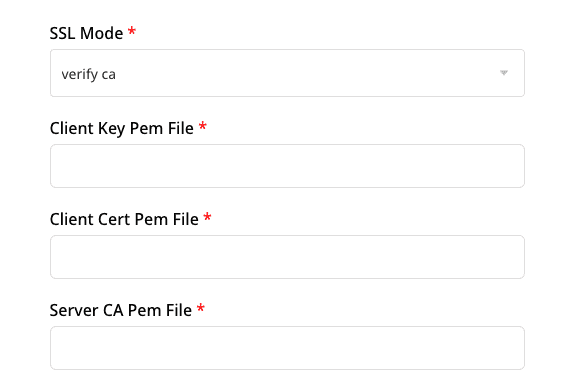
To use verify-ca as the SSL mode while configuring your PostgreSQL destination, you need to copy the contents of the following three files from your SSL certificate:
- Client Key Pem File
- Client Cert Pem File
- Server CA Pem File
The following steps demonstrate how you can create a new SSL certificate in Google Cloud SQL and obtain the above-mentioned credentials:
- Go to your PostgreSQL instance in your Cloud SQL console.
- In the left panel, click Connections and go to the SECURITY tab.
- Under Manage client certificates, click CREATE CLIENT CERTIFICATE.
- Assign a unique identifier for your SSL certificate and click CREATE. Your new SSL certificate will be created, as shown:
- Finally, copy the contents of the three fields and paste it in the RudderStack dashboard settings as seen below:
IPs to be allowlisted
To enable network access to RudderStack, you will need to allowlist the following RudderStack IPs:
- 3.216.35.97
- 23.20.96.9
- 18.214.35.254
- 54.147.40.62
- 34.198.90.241
- 100.20.239.77
- 52.38.160.231
- 34.211.241.254
- 44.236.60.231
- 3.66.99.198
- 3.64.201.167
- 3.66.99.198
- 3.64.201.167
FAQ
RudderStack does not create the corresponding PostgreSQL tables when I press on 'sync'. What do I do?
- Firstly, check the status of your data sync in the RudderStack dashboard.
- Make sure you have set up the user permissions for your PostgreSQL instance.
- Check if your database is accessible to RudderStack by allowlisting the RudderStack IPs.
- Ensure that all the security group policies are appropriately set.
How does RudderStack handle reserved words?
There are some limitations when it comes to using reserved words in a schema, table, or column names. If such words are used as event names, traits or properties, they will be prefixed with a _ when RudderStack creates tables or columns for them in your schema.
Also, it is important to note that integers are not allowed at the start of the schema or table name. Hence, RudderStack prefixes such schema, column or table names with a _.
For instance, '25dollarpurchase' will be changed by RudderStack to '_25dollarpurchase'.
How does RudderStack handle cases when loading data into PostgreSQL?
RudderStack converts the event keys into the lower case before exporting the data into PostgreSQL, so that it does not create multiple tables if the event name is written in different cases.
Contact us
For more information on the topics covered on this page, email us or start a conversation in our Slack community.